How to configure role permissions
AI Agent Connector uses Magento's role-based access control (ACL) to determine which tools each admin user can access. You can also configure per-role restrictions for the Database Reader tool.
Tool permissions
-
Navigate to System -> Permissions -> User Roles and click on a role.
-
Open the Role Resources tab.
-
Expand the MCP Tools section.
-
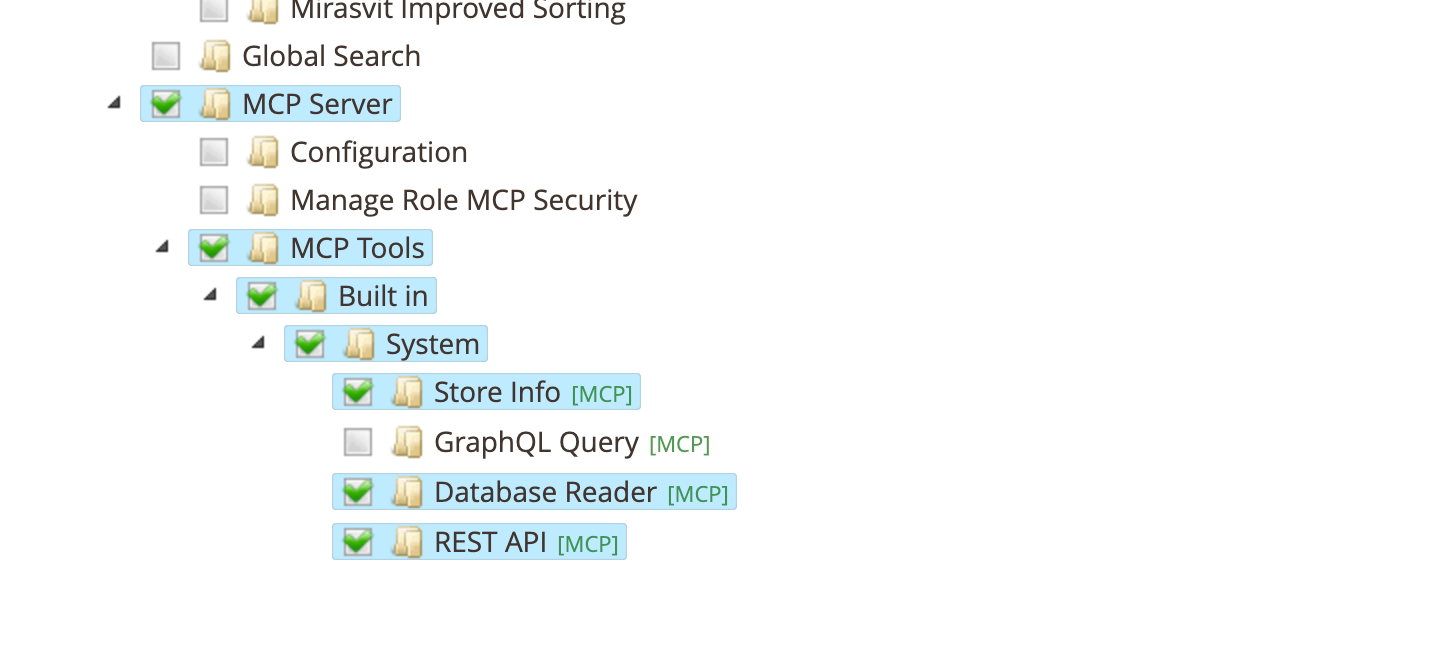
Enable or disable individual tools. The tree is built dynamically from all registered tools:
- MCP Tools
- Built in
- System
- Store Info — access to store configuration data
- GraphQL Query — execute GraphQL queries and mutations
- Database Reader — execute read-only SQL queries
- REST API — call Magento REST API endpoints
- System
- Built in
Third-party tools appear as additional groups under MCP Tools, organized by vendor and module.
- MCP Tools
- Click Save Role.
The AI client can only use tools that are enabled for the authorizing admin user's role. If a tool is disabled in the role, the AI client will not see it in the tool list.
Database Reader restrictions per role
In addition to ACL-based tool access, you can configure per-role restrictions for which database tables the Database Reader tool can access.
- Navigate to System -> Permissions -> User Roles and click on a role.
- Open the MCP Info tab.
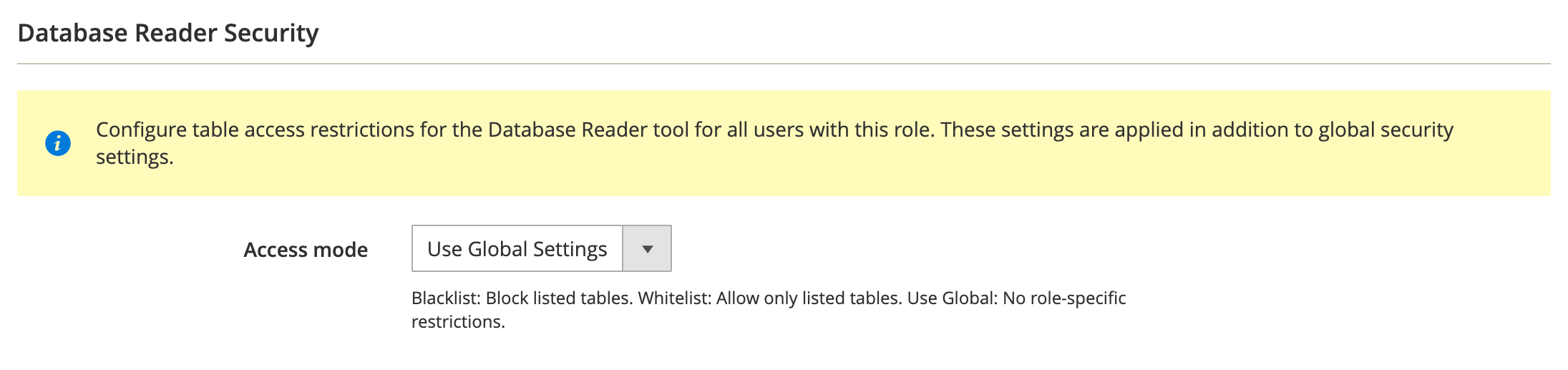
- Configure the Database Reader Security section:
-
Access mode:
- Use Global Settings: inherits the access mode from global configuration
- Blacklist: tables matching the patterns are blocked for this role
- Whitelist: only tables matching the patterns are accessible for this role
-
Table patterns: one pattern per line. Use
*as a wildcard. These patterns are applied in addition to global settings.
- Click Save Role.
How global and role patterns combine
Both global and role-specific patterns are enforced. Role patterns add restrictions on top of global settings — they cannot grant access to tables blocked by global configuration.
Example:
- Global setting: whitelist mode with
sales_*,catalog_* - Role setting: whitelist mode with
sales_order
Result: the user with this role can only access the sales_order table. Even though the global whitelist allows all sales_* and catalog_* tables, the role whitelist further restricts access to just sales_order.
MCP Tools permissions tree
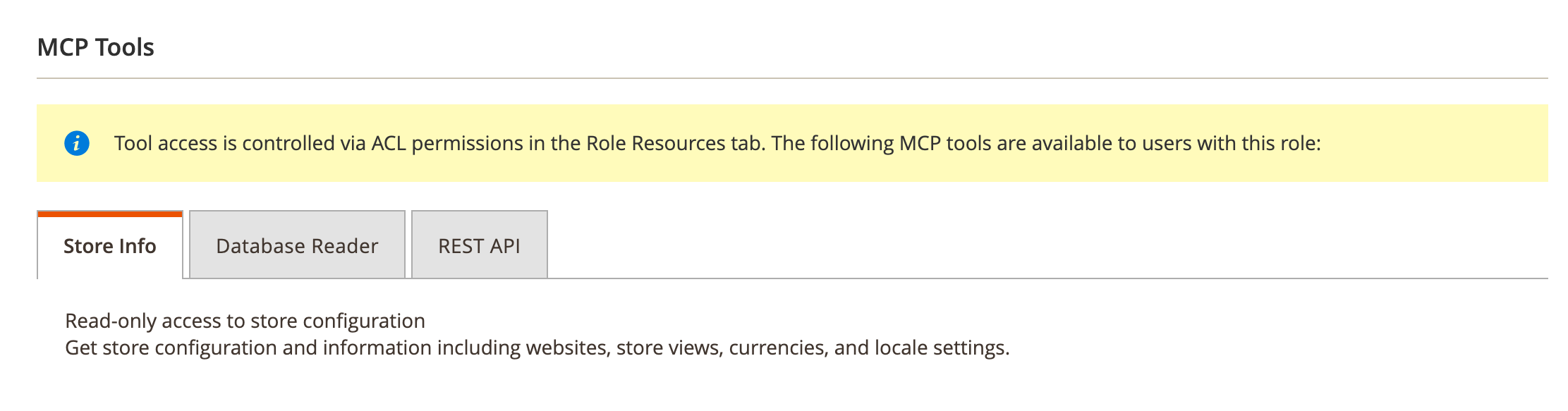
The MCP Info tab also displays the full MCP Tools permissions tree, showing which tools are available to the role. This mirrors the ACL configuration from Role Resources and serves as a quick reference.